We are going to switch things up a bit and walk you through a retelling of a ransomware attack through the eyes of a business owner. Usually when we talk about these types of threats, we approach it from our perspective and talk about what you should do to prepare and what the threats are, but we wanted to try to show you what an event like this could feel like, for you, in your position, and in your own eyes. We hope that this will raise awareness of how crippling an event like this can be on your company, and we hope you let us know if this perspective helps you, your colleagues, and your staff get a more personal sense of what ransomware can do. Enjoy!
What a day it has been!
Typically, when I have a day like I just had, I wouldn’t sit here and write about it, but since our story is sure to help people, I thought that I should. Besides, my adrenaline is still pumping, and I don’t think I can sleep yet anyway.
The day I had was terrifying but started just like any other. I got through my morning routine and made my way to the office. I even stopped at the shoppe to get coffee. Once I entered the building I knew something was wrong. I had two employees beat me to the office. They were milling around almost aimlessly in the hallway. Before I even reached my desk, I was inundated with bad news.
“We are locked out!”
“What are we supposed to do?”
After getting past my employees into my office, I tried to ascertain what the problem was. It was evident very quickly that we had a major problem on our hands.
@!#?! It’s ransomware! I can’t believe it!
It could only be ransomware.
I wasn’t sure what allowed this to happen. Did one of my staff click on a bad link? Was our network vulnerable from the get go? Since the ransomware had spread onto the network, I could tell that the affected computer had to be used to manage other endpoints, pushing ransomware to all the endpoints the terminal had managed. This is why the computers that were on the network had the same message. This means that it ended up stealing usernames and passwords to open each endpoint and lock down the data on them.
It is during this period that the entity that unleashed this beast on us would look to take as much data as they could. It turned out that my company was using a global password configuration and the ransomware spread throughout our network like wildfire. So, when I was met with the message, I knew exactly what I was dealing with.
I never for a second thought that it would happen to us. Our business doesn’t deal with major financial institutions or medical records, so it would seem to keep us safe from these kinds of security breaches. I guess I’m just the latest person to ask, “why us?”
For those who don’t know, ransomware is any type of malicious application that “kidnaps” the data and holds it for ransom. It can shut down the files of a single computer, or in our experience, it can spread over the network to several endpoints; effectively shutting down operations for long stretches of time. I wanted to share my experience to help you know what to expect if you are one of the unfortunate business owners that have to have all the answers.
Don’t Panic
No matter how prepared you are for something like this, at first, you feel panic. Typically, you are immediately overwhelmed and are left kind of dumbfounded, glancing around the room, looking for answers that aren’t there. Regrettably, if you are doing that, the damage is done and there is nothing you can do about that. Scenarios race by in your head and the more they turn negative, the more the fear builds up in the base of your neck, in your throat, or in the pit of your stomach. You need to stay as calm as you can and begin troubleshooting immediately. The thing about ransomware is you can’t just wait it out. Once that wave of fear subsides, you have to make a measured response, because you likely have people that are on the clock, and an IT infrastructure that is locked down.
After the initial shock, I went to work.
Fighting Ransomware
I learned quickly that there are two main types of ransomware:
- Locker - Malware that locks the computer or device.
- Crypto - Malware that encrypts data and files.
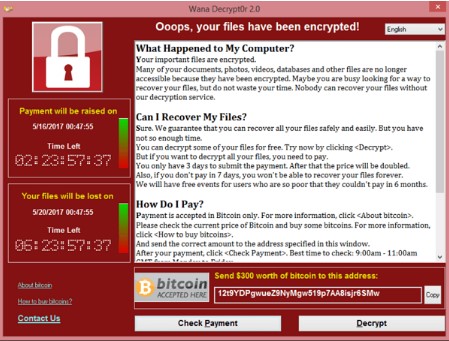
The type we were unfortunate enough to encounter was WannaCry, a crypto ransomware that has infected millions of people worldwide by taking advantage of an unpatched Windows vulnerability. As a small business, our technology management was pieced together, but after this event, and all we’ve learned from it, we will definitely be sure to make our staff cognizant of how to avoid situations like this.
For us, we had three machines infected with a variant of WannaCry. The ransomware stated that if we pay $300 in Bitcoin for every machine that was locked, we could get our data back... and the clock was ticking, literally.
At that point, we had three options. We could abandon the machines and buy new ones, we could pay the hackers that had encrypted our data, or, we could attempt to restore our systems.
Part of me wanted nothing more than to just abandon the machines, bust our IT budget for the year and be done with it. We instead decided to try to restore the machines to a prior version, because paying the hackers was never a real option. First of all, any person that could inflict this kind of fresh hell on a small business was not to be trusted; and, I felt if I were to pay the ransom, there was no guarantee that we would a) get our files back; or, b) not get harassed again by the same people.
Since cost was a factor, we reached out the IT professionals at Telesys Voice and Data, and they walked us through the process of restoring our terminal and the two machines connected to it. Luckily for us, they had the knowledge and expertise to help us get through this horrible time. We will lose quite a bit of work, but, as of right now, it looks like we are going to come out of this whole thing much better than the majority of companies that have dealt with it.
I know we were lucky. I know we have to try harder. I know we aren’t out of the woods just yet, but I have to thank the people at Telesys Voice and Data. They really came through for us!
Ransomware attacks are rampant. If your small business isn’t proactive about its network security and if you don’t train your people on what to look for, you could be dealing with a problem that could potentially sink your business. For more information about ransomware, WannaCry, or other threats your organization faces today, call us today at (800) 588-4430.