Chances are you have a Google account, whether it’s for business or personal use. It’s more accessible today than ever before and provides a solid way to gain access to several important features and accounts. Considering how much can be done with a Google account, users forget that they can put their security and personal data at risk. Here are some ways that your Google account is at risk, as well as what you can do to fix it.
Telesys Voice and Data Blog
There will never be a time that we are not committed to improving the security of businesses. To continue striving for this goal, we’re dedicating this week’s tip to describing some solutions that can assist in locking a business and its data down.
When we write about Net Neutrality, we typically write about how it is designed to keep the telecommunications conglomerates, who make Internet service available to individuals on the Internet, honest when laying out their Internet service sales strategy. One way to put it is that without net neutrality in place, the Big Four (which are currently Comcast, Charter, Verizon, and AT&T) have complete control over the amount of Internet their customers can access.
Unfortunately, one of the most effective defenses against phishing attacks has suddenly become a lot less dependable. This means that you and your users must be ready to catch these attempts instead. Here, we’ll review a few new attacks that can be included in a phishing attempt, and how you and your users can better identify them for yourselves.
Imagine a world where there wasn’t a singular dishonest being. Passwords would simply vanish from our everyday lives, as we would not be paranoid of a breach or other forms of cybercriminal activity. The harsh reality is this will never become reality. Even worse, the cybercriminals don’t just skim for lack of passwords. Instead, the dishonest criminal goes even further; they take advantage of common or recurring passwords. So how do you know if your password practices are leaving you vulnerable? Google is here to help.
Wi-Fi has swiftly become one of those amenities that we just expect to have, including in the workplace. While it does make work around the office more convenient, it should not be at the cost of your security. To help prevent this, we’re reviewing a few key Wi-Fi security considerations to keep in mind.
Organizational cybersecurity has to be a priority for every business. These days, companies are getting hacked left and right and being exposed to some of the very worst malware ever created. Today, we will take a look at some cybercrime statistics that will put in perspective just how damaging cybercrime is.
Most companies have some sort of regulation they need to stay compliant to, and 2020 seems to be a landmark year. This year, companies have to deal with end-of-life upgrades, the development of new privacy laws, as well as the existing regulatory landscape. Let’s take a look at why compliance is important and what to expect in the year ahead.
Today, everything we do on the computer and on our phones creates data. Organizations that are good at utilizing this data, often look to capture everything that they can. This can leave the individual searching for a way to keep his/her data secure. Let’s take a look at some of the best practices used to prioritize individual data privacy.
More than any time before, cybersecurity has to be a major consideration for businesses. It is, in fact, one of the biggest problems the modern business has to face day-in and day-out. Shortage in cybersecurity talent and antiquated strategies are making it difficult for businesses to find the knowledgeable resources that will help them work to secure their network and data from threats to the business.
It’s fair to say that most business owners aren’t cybersecurity experts. That’s why there is such a large investment in cybersecurity solutions. That outlay is justified, sure, but is it effective? Today, we’ll talk a little bit about network and cybersecurity, and how all the capital investment in the world may not actually keep your network secure.
The professional services space is filled with important information. Lawyers, accountants, doctors, and many more professionals have access to some of the very most personal information available. For this reason, they are continuously targeted by hackers. Since October is cybersecurity awareness month, we thought we would take a look at modern cybersecurity practices to see which ones were working best for professional services firms.
Your business’ data is precious, and it goes without saying that there are plenty of entities out there that want to get their grubby little fingers all over it. This is especially the case these days, when credentials and remote access tools can be purchased on the black market and leveraged against organizations of all sizes. If you don’t take action to keep your data secure from unauthorized access, you could face steep fines from compliance issues, not to mention the embarrassment of not being able to protect your organization’s data.
In the late 1970s and early 1980s, Bell telephone companies were making a mint off of offering the ability to call your friends and family that lived outside your predefined region, charging up to $2 per minute (during peak hours) for long distance calls. The problem for many people was that these regions kept shrinking. Some people decided to combat this costly system by reverse engineering the system of tones used to route long-distance calls, thus routing their own calls without the massive per-minute charges demanded by long-distance providers. These people were called Phreakers, and they were, in effect, the first hackers.
Cloud-based databases are valuable for businesses on plenty of levels, but when you consider how much risk you expose your organization to by using a public cloud over a private solution, you suddenly start to realize that the ramifications could be far beyond repair. Compared to the public cloud, a private solution presents a greater opportunity for security, flexibility, and customization.
All that stands between hackers and your accounts’ data, be it personal information or sensitive business info, is a measly string of characters that may (or may not) be complex enough to thwart their attacks. We’re talking about your passwords, and for many businesses, they are the only thing protecting important data. We’ll walk you through how to make sure your passwords are as complex as possible, as well as instruct you on how to implement additional security features to keep your data locked down.
Spam is a major hindrance when running a business that relies on email, but it’s easy to protect your employee’s time from the average spam messages with the right technological support. Unfortunately, hackers have adapted to this change and made it more difficult to identify scam emails. More specifically, they have turned to customizing their spam messages to hit specific individuals within organizations.
Each year there are changes that need to be made in the way that organizations manage their IT security. In 2017, ransomware burst on the scene in full force, and cyber security strategies reacted, coming up with fully managed security platform that remediate issues better, and cost organizations far more than they would have spent on IT security just a short time ago. In 2018, the same problems persist, while other developing technologies threaten the natural order of things. Today, we will look at how cybersecurity is being approached in 2018.
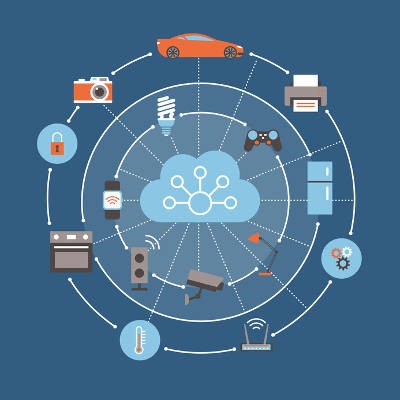
The Internet of Things means a lot more than just enhanced connectivity. In particular, you’ll have a considerable security risk associated with the Internet of Things. It’s clear that the more devices accessing a network, the more risk will be associated with that network, which is where the inherent risk of the Internet of Things comes into play. How can you control the number of devices accessing your network, and thus secure your business from the Internet of Things?
Understanding why security is such an issue for Internet of Things devices is critical to keeping your business secure from these devices.
Too Many Devices
The more threats are associated with a particular industry, the more likely you’ll encounter a threat. This is not conjecture--it’s reality. When you consider how many devices now have connectivity compared to the past, you might realize that these fears regarding the Internet of Things aren’t unfounded. You should go about organizing your business’ security by imagining what you would do in a worst-case scenario in which at least one of these devices makes it past your organization’s defenses. All it takes is a single weakness to bring down an entire network.
The issue with these devices is that they are often those that you wouldn’t expect to traditionally have such connectivity. For example, you might not immediately think of cars, kitchen appliances, watches, or thermostats to have such functionality. These can be difficult to plan for if you’re not careful.
Patches and Updates
When there are a lot of devices accessing a network, chances are that at least one of them won’t be up to snuff with its updates and patches. The incredible vastness of the Internet of Things all but guarantees that at least one of these devices is going to be out of date, placing your organization at risk. To make things even worse, some Internet of Things devices are created based off a trend that could very well be obsolete soon afterward, meaning that developers might not see the need to support the device beyond that timeframe. For example, if a device sells poorly and was created only to meet a specific need in the industry at the time, the developer may choose not to support it anymore as the investment simply isn’t worth the return.
Even if you can’t control the devices of others, you can control the ones that access your organization’s sensitive data. You can start by taking a look at the specific permissions of your business’ users and their devices. A good practice is to never give employees access to information that they don’t need to do their jobs properly. After all, the more people who can access data, the more likely that a device could be compromised and expose that data to threats.
Telesys Voice and Data can help your business manage devices and access control on its network. To learn more, reach out to us at (800) 588-4430.
One of the inevitabilities of working with the cloud is that you have to face a tough question; what kind of compliance requirements are there for cloud-based data? If you’re storing data for your business in a cloud-based environment, it becomes your responsibility to know where and how this data is stored--particularly if you’re not the one doing the actual cloud hosting. How do you maintain compliance when you seemingly have so little control over how your computing platform is managed and maintained?
It all starts by asking your cloud provider specific questions about how compliance is handled, as well as what terms are written into the agreement that you have with them. We’ll go over some of the details that you’ll need to address.
The Cloud Can Be Tampered With
Naturally, one of the major concerns that businesses might have about cloud compliance is the idea of how this data is being managed, maintained, stored, and transferred. This also means that it can be changed or intercepted while it is in transit. Therefore, the key concern is that data could be changed without the user’s knowledge. Those who are concerned about the legal ramifications of this should focus on learning who is hosting the data, how it is being maintained, how it is being transported from the hosting site to your infrastructure, and who can see this data. This line is further blurred by the differences between the public and private cloud. In other words, is your data being stored alongside someone else’s data? Are there partitions put into place that limit access based on role and organization? The question of security is of the utmost importance and will be a major point that you’ll need to hit for compliance’s sake.
What Can You Do?
Using the above statements as a springboard, you’ll need to think about how your business plans on securing cloud-based data and ensuring its compliance with any regulations your organization is beholden to. You start by first assessing just how deep into cloud computing your organization actually is. Depending on the importance of certain data, you may decide that a combination of private and public cloud platforms present the ideal solution. For sensitive information, an internal network or private cloud is ideal, while less sensitive or important data is stored elsewhere.
Next, you’ll need to consider who is managing this data, and what kind of agreements you will have to make to guarantee its safety. Is it being managed by an in-house department or a third party? If it’s a third party, for example, you’ll need to determine responsibilities and consequences of failing to adhere to compliance guidelines. It’s also important that you know what types of security and backup solutions are being used to protect your assets.
Since your organizational reputation and integrity is on the line, your best bet is to find a way to design, deploy, and support a private cloud solution onsite for any data that could possibly be subject to regulatory compliance. Otherwise, you may find that any cloud-hosting company or colocation service won’t have your immediate needs top of mind.
Telesys Voice and Data can help your business ensure security of your cloud solutions. To learn more, reach out to us at (800) 588-4430.
Mobile? Grab this Article!
Tag Cloud